ElBlo
If life gives you fonts, start tunneling
Given Google’s infrastructure, if you can access one Google service over TLS (even to download a font), it is possible to tunnel traffic over ssh using only that service’s IP.
TL;DR: GFE serves all Google services from most of the IPs. Google Cloud offers a TLS bridge to connect to a GCE instance via SSH, and you can use this to create a SOCKS5 proxy and tunnel your traffic through it.
Disclaimer: This is not something Google recommends. The information in this post comes from Google’s public documentation. I work at Google, but opinions on this post are my own.
Sometimes you are connected to a not-so-friendly network that restricts your internet access, like a captive portal. If the restriction is enforced via an IP:port allowlist, and at least one Google IP is allowed for TLS connections, you might be able to bypass the policy.
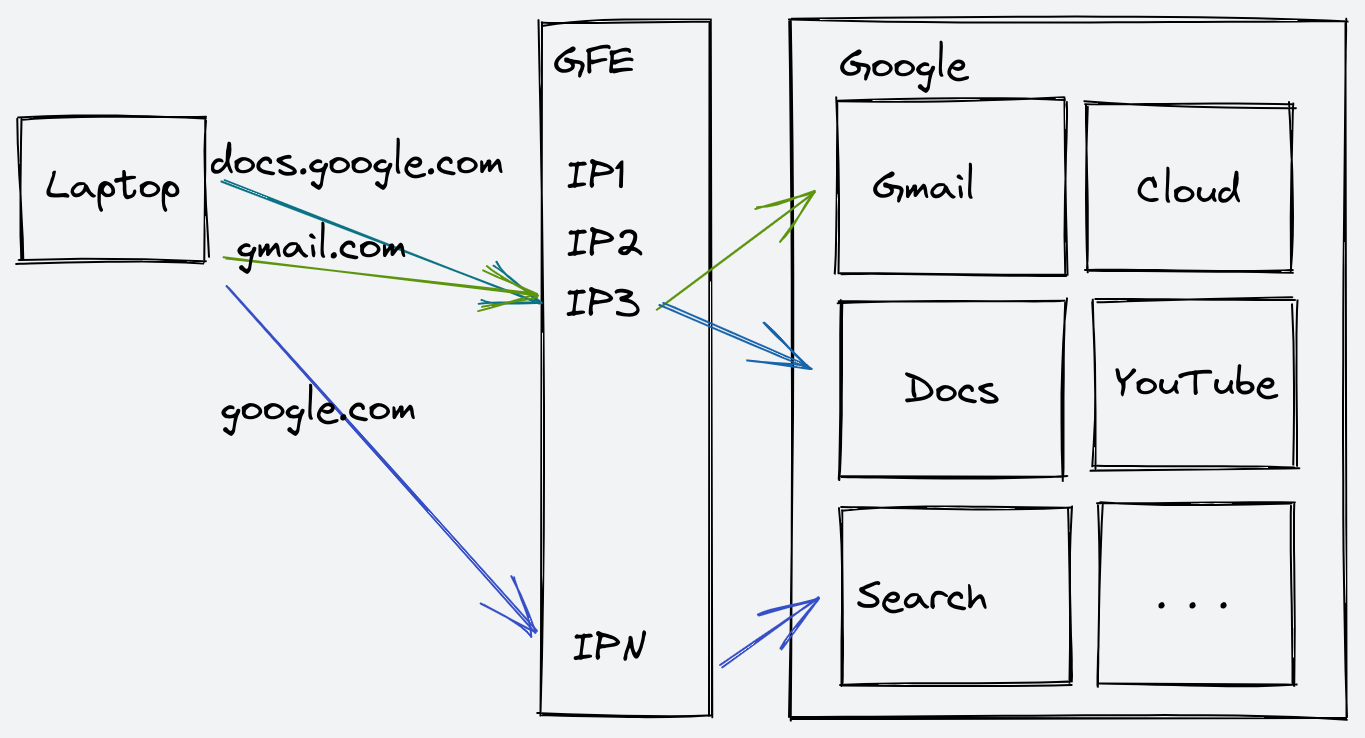
According to the Google Cloud Documentation1, all user traffic that connects
to a Google Service (even Google Apps or Firebase!) goes through a service
called Google FrontEnd (GFE). If, for example, you want to
download a font from fonts.gstatic.com, any IP address from the GFE range
will be able to serve it to you. Make the HTTPS request to an IP from
the GFE, and it will give you the response from the right backend service.
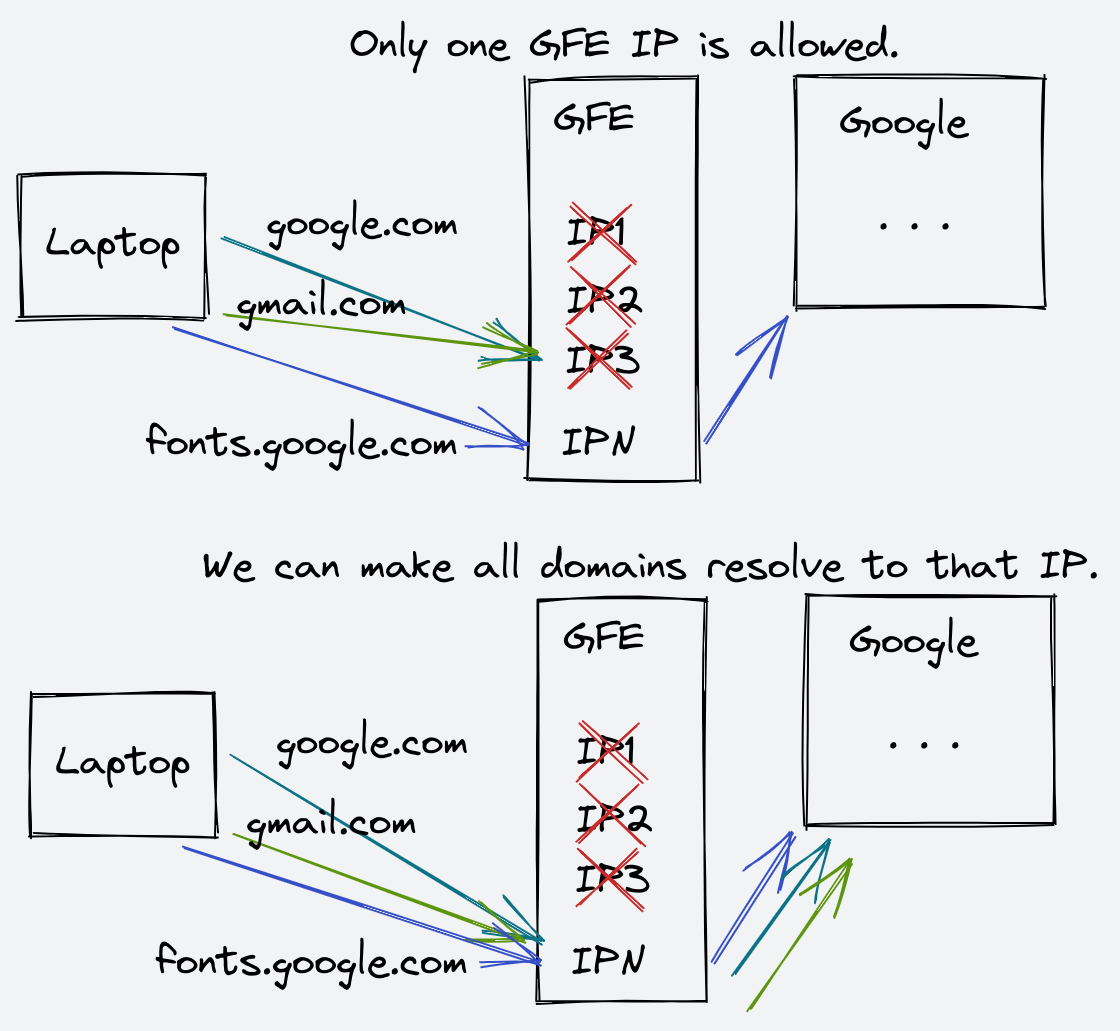
Now if your network restrictions allow for at least one
Google IP (be it fonts or any other assets), you can leverage that to get
access to other Google content: change the DNS mappings in /etc/hosts
for each of the Google domains that you care about and make them point to the
allowed Google IP. Once a TLS connection is established, it becomes harder to tell the difference between a connection to fonts.google.com and
any other domain.2
Having access to Gmail or Hangouts is nice, but you can do better. You can get access to the whole internet if you have a VM hosted in Google Compute Engine (GCE). Ideally, you would like to connect to the VM via ssh and create a SOCKS5 proxy, but you can’t connect to the VM external IP because it is most probably blocked.
One of the Google services that is available in GFE, is the Identity-Aware Proxy3 (IAP), which lets you access internal resources over TLS after you identified yourself.
Google’s IAP can do TCP forwarding4, which tunnels the TCP
connection over TLS. The gcloud app will let you tunnel SSH via IAP using the
--tunnel-through-iap flag5.
When you connect via ssh, you can use the -D option to create a socks5 proxy
and forward your local traffic through it. The command is something like this:
$ gcloud compute ssh "vm-name" --tunnel-through-iap -- -N -p 22 -D localhost:5000
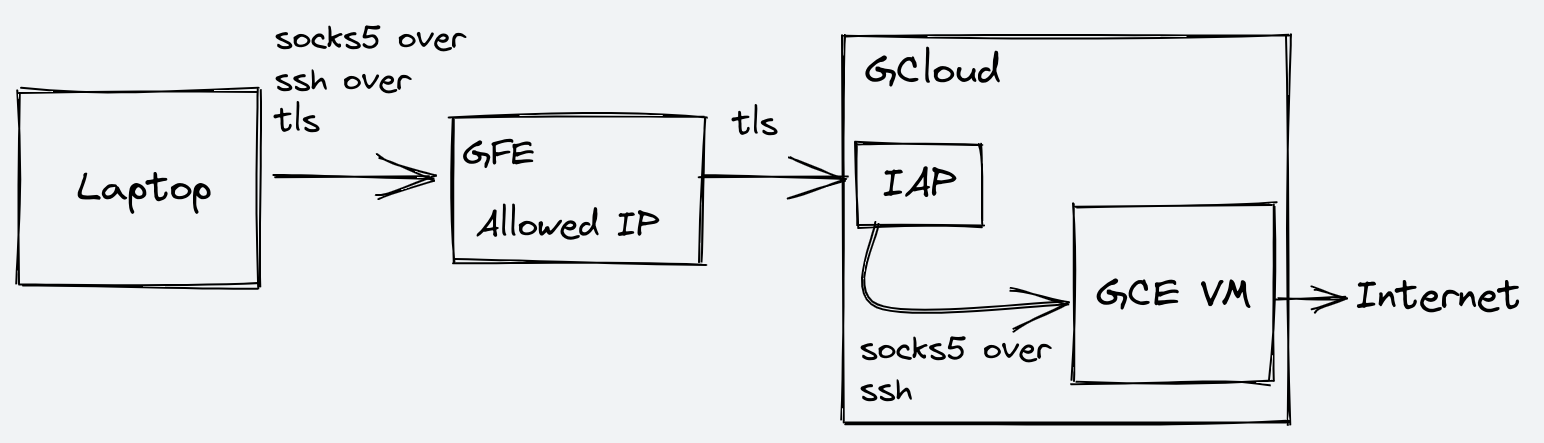
Note that there are other ways that could also bypass some of the network restrictions. For example, having an App Engine service acting as a proxy might work as well, or doing some other TCP forwarding from IAP. Using the IAP tunnel is the easiest one I found, as I already had a GCE VM.
Summary of steps needed:
- Download and install the
gcloudapp. - Set up a GCE VM that you can ssh into with the
gcloudapp. - Identify if the network allows connections to a Google-owned IP over TLS on
port
443. - Add entries in
/etc/hostsfor all the Google URLs you are trying to access. - Use the
gcloudcommand to establish a tunnel to the GCE VM using the IAP. - Configure your system/browser to use
localhost:5000as a SOCKS5 proxy.
I Hope this helps someone :)
-
https://cloud.google.com/security/encryption-in-transit#end_user_internet_to_a_service ↩︎
-
This is not infallible: a network could still block some domains by doing deep packet inspection and checking that the Server Name Indicator (SNI) field in the TLS Handshake is in an allow-list. ↩︎
-
https://cloud.google.com/iap/docs/tcp-forwarding-overview ↩︎
-
https://cloud.google.com/sdk/gcloud/reference/compute/ssh#--tunnel-through-iap ↩︎